Microsoft's new OS isn't perfect, but it is what Windows Vista should have been. Here's a hands-on look at the version that's beginning to hit PCs.
For most people who are considering moving to Windows 7, October 22 is D-Day. On that date Microsoft's newest operating system lands on store shelves, both as a shrinkwrapped upgrade and preinstalled on new PCs. For some folks, though, D-Day has already arrived. Microsoft has issued the final RTM (release to manufacturing) version of Windows 7 to large companies that buy Windows via volume licenses, as well as to IT pros who belong to its Technet service. The Windows Vista era is officially drawing to a close--although you could argue that it never really quite started--and the Windows 7 one is under way.
And that promises to be a good thing, whether you're a satisfied Vista user, a disgruntled one, or a Windows XP holdout who has been waiting for something better. Windows 7 feels like an anti-Vista: Unlike that OS, for instance, it doesn't try to dazzle you with flashy new visual effects. With the removal of Vista applications such as Photo Gallery and Movie Maker, Win 7 actually does fewer things than Vista did. Even its unprepossessing name is a change from the epic-sounding monikers that began with the unfortunate Windows Millennium Edition.
But Windows 7's lack of glitz is a huge part of its appeal. Unlike the increasingly chaotic and annoying Microsoft OSs that preceded it, Windows 7 is designed to stay out of your way so that you can get stuff done. It smartly addresses Windows annoyances both new (User Account Control) and old (the system tray). And the final version I've been using seems to realize the promise of the rough drafts we started testing last October.
Windows 7 isn't without its warts, but I haven't been so impressed by a new Microsoft operating system since Windows 2000 debuted close to a decade ago. Here's a quick look at some of its best features, a few drawbacks, and areas where reserving judgment makes sense. (Much more PC World coverage is on its way, including an in-depth review with speed benchmarks, upgrade tips, and Windows 7 system reviews.)
The Good...
The OS is less piggish: One of the many regrettable things about the initial version of Windows Vista was that its signature feature--the splashy Aero environment--was too much of a resource hog to run well on many early-2007 PCs (even those that had been promoted as Vista-capable). The PC World Test Center hasn't benchmarked the shipping version of Windows 7 yet--stay tuned--but all signs point to this OS being sprightly enough to perform decently on all current systems, including those allegedly underpowered, pint-size machines known as netbooks.
The taskbar has been reinvented: It's amazing how little the taskbar and its system tray have changed since Windows 95. In Windows 7, they both undergo sweeping, long-overdue makeovers. For the most part, the results are extremely pleasing.
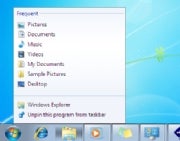 The new taskbar's default style does away with text labels and relies solely on program icons, therefore making better use of screen space. Its thumbnail previews--an improvement over Vista's--work well even when you have multiple windows open for one application. And the new Jump Lists feature gives you right-click access to context-sensitive menus of options (such as the ability to play shuffled music in Windows Media Player) even before you've launched an application. Even the nub on the right edge of the taskbar, which you can click to reveal the desktop, is a welcome, subtle enhancement. (One taskbar quibble: The border around running apps in the taskbar isn't a clear enough cue to distinguish between them and those that aren't currently active.)
The new taskbar's default style does away with text labels and relies solely on program icons, therefore making better use of screen space. Its thumbnail previews--an improvement over Vista's--work well even when you have multiple windows open for one application. And the new Jump Lists feature gives you right-click access to context-sensitive menus of options (such as the ability to play shuffled music in Windows Media Player) even before you've launched an application. Even the nub on the right edge of the taskbar, which you can click to reveal the desktop, is a welcome, subtle enhancement. (One taskbar quibble: The border around running apps in the taskbar isn't a clear enough cue to distinguish between them and those that aren't currently active.)
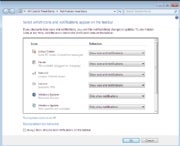 The system tray--which is officially called the notification area, although I don't know anybody who calls it that--is no longer one of Windows' most aggravating "features." When you install new applications, any associated system-tray applets are cordoned off in a holding pen, where they can't clutter up the tray and can't use word balloons to pester you with information that you may or may not care about. You can also choose to have an applet appear in the system tray but in bound-and-gagged form, so it can't pop up messages. Microsoft has also dramatically reduced the volume of distracting messages from Windows itself, courtesy of Action Center, which queues up system alerts so that you can check them out at your convenience.
The system tray--which is officially called the notification area, although I don't know anybody who calls it that--is no longer one of Windows' most aggravating "features." When you install new applications, any associated system-tray applets are cordoned off in a holding pen, where they can't clutter up the tray and can't use word balloons to pester you with information that you may or may not care about. You can also choose to have an applet appear in the system tray but in bound-and-gagged form, so it can't pop up messages. Microsoft has also dramatically reduced the volume of distracting messages from Windows itself, courtesy of Action Center, which queues up system alerts so that you can check them out at your convenience.
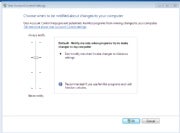 UAC is now tolerable: Windows Vista introduced User Account Control, which tries to warn you of attempts by viruses and other malware to tamper with your system. But it essentially has two settings: So Annoying You Click Without Thinking, and Off. In Windows 7, you get two intermediate settings that alert you only if a program changes settings, with or without the melodramatic screen-dimming effect. This new version is such a reasonable approach that it's even more mysterious how Microsoft could have botched the Vista version so badly.
UAC is now tolerable: Windows Vista introduced User Account Control, which tries to warn you of attempts by viruses and other malware to tamper with your system. But it essentially has two settings: So Annoying You Click Without Thinking, and Off. In Windows 7, you get two intermediate settings that alert you only if a program changes settings, with or without the melodramatic screen-dimming effect. This new version is such a reasonable approach that it's even more mysterious how Microsoft could have botched the Vista version so badly.
Libraries collect your files: For years, Microsoft has tried to train Windows users to store all of their personal files in one place, helpfully providing a folder named My Documents for that purpose. Many of us blithely ignore the suggestion and store stuff willy-nilly around our hard drives. A new feature called Libraries splits the difference by giving you virtual folders for documents, music, photos, and videos that combine the contents of whichever folders you specify into one unified view. The Pictures Library, for instance, can show all your photos even if they're stored in a dozen different places. Still, there's room for improvement--Libraries would be even more useful if they were integrated with the existing Saved Searches feature, which creates another, separate form of virtualized folder.
The Bad...
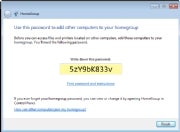 HomeGroups are disappointing: HomeGroups sound like a nifty idea--a way to share folders full of media and documents between PCs across a network, so you can peruse photos stored on a desktop in the den from your laptop in the living room, for instance. But Microsoft's implementation is surprisingly half-baked: Rather than letting you specify a password during setup, for instance, it assigns one consisting of ten alphanumeric gibberish characters and tells you to write it down. And HomeGroups work only if all the PCs in question run Windows 7. A version that also worked on XP, Vista, and--dare I say it?--Macs would have been far cooler.
HomeGroups are disappointing: HomeGroups sound like a nifty idea--a way to share folders full of media and documents between PCs across a network, so you can peruse photos stored on a desktop in the den from your laptop in the living room, for instance. But Microsoft's implementation is surprisingly half-baked: Rather than letting you specify a password during setup, for instance, it assigns one consisting of ten alphanumeric gibberish characters and tells you to write it down. And HomeGroups work only if all the PCs in question run Windows 7. A version that also worked on XP, Vista, and--dare I say it?--Macs would have been far cooler.
Windows Update can still shut you down: There's no reason to believe that Windows 7 will require less patching than earlier versions of the OS. If you use Windows Update the way Microsoft recommends, however, your computer may still demand that you shut it down so it can update itself, or it may decide to devote an extended amount of time to installing updates when you try to reboot it. In the largely compliant and considerate Win 7, this aggressive approach to updates is a flashback to Windows' pushy past.
You can't upgrade Windows XP: If you want to upgrade a PC from XP to 7, you'll need to start anew, reinstalling all of your apps and re-creating your settings. (Windows Vista users can opt to install 7 on top of their current OS, although not in every possible scenario.) Microsoft's decision not to enable XP-to-7 upgrades is defensible--a fresh install will probably be more reliable than one plunked down on top of XP's eight-year-old underpinnings--but it will scare off some XP users who would probably love Windows 7 once they got it up and running.
...and the Unknown
How bad will compatibility issues be? Windows 7 looks and works differently than Windows Vista does, but below the surface it isn't radically different. That should make for fewer headaches with incompatible drivers and software--and indeed, it helped even the earliest Windows 7 preview versions run surprisingly smoothly for prerelease operating systems. But as millions of people install Windows 7 on an endless array of PCs, undoubtedly some of them will encounter problems that Microsoft didn't anticipate. (I've run into setup quirks and driver issues with the Windows 7 RTM version myself, but I've been able to work around them--by installing from a USB drive rather than a DVD, for instance.)
 Will hardware companies take to Device Stage? This new feature gives your printer, camera, and other peripherals information centers of their own, which hardware manufacturers can customize with features such as links to online manuals and troubleshooting tools. But unless companies invest the time to build useful Device Stages, this could be another Microsoft bright idea that doesn't go much of anywhere. Also, parts of Device Stage look short on substance (giant photorealistic renderings of your peripherals!) and others look potentially irritating (printer companies hawking ink cartridges right inside your OS!). All in all, I don't think it'll be a tragedy if Device Stage doesn't catch on.
Will hardware companies take to Device Stage? This new feature gives your printer, camera, and other peripherals information centers of their own, which hardware manufacturers can customize with features such as links to online manuals and troubleshooting tools. But unless companies invest the time to build useful Device Stages, this could be another Microsoft bright idea that doesn't go much of anywhere. Also, parts of Device Stage look short on substance (giant photorealistic renderings of your peripherals!) and others look potentially irritating (printer companies hawking ink cartridges right inside your OS!). All in all, I don't think it'll be a tragedy if Device Stage doesn't catch on.
Is touch input a boon or a boondoggle? Windows 7 is the first version of the OS with special support for multitouch input--for example, if it notices that you've opened the Start menu with your finger rather than the mouse pointer, you'll see a roomier version of the menu that takes less precision to navigate. Of course, all of that requires a multitouch-capable PC, and only a handful (such as the upscale HP TouchSmart) are on the market. Windows 7's arrival might prompt a profusion of interesting new touch-enabled PCs--but even then, what we really need are interesting touch-enabled applications. (Microsoft's touch demos have tended to feature such ho-hum uses as fingerpainting in Windows' own Paint program.)
The Bottom Line
Last year Microsoft tried to repair Windows Vista's reputation by pretending it was a new OS code-named Mojave and getting focus-group subjects to say nice things about it. If the company had released a Vista back in 2007 that was as pleasant to use as Windows 7 is, the OS might never have had image problems in the first place.
Even when an OS upgrade is as appealing as this one, it makes sense to proceed with caution. Many of the people who grab Windows 7 at the first possible opportunity will be happy they did. But I suspect that some of the folks who wait a bit more--installing the new OS only after other people have discovered unexpected glitches with applications and drivers--will be even happier. And if you're using an aging PC, it's perfectly sensible to hold off on Windows 7 until you're ready to buy a brand-new system that's designed to run it well.
My advice for Windows users, then, is this: Get Windows 7, but on your own schedule. It'll be ready when you are--and you'll almost certainly consider it an improvement over whatever version of Windows you're using now.

![[Image]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEghSZtUkcW-TT7jRfFV5r027XdGSdGt58z8mWO03bTlGvHFUAQ97eed1BK1Xho07AojPC2QtJ4CL-PFg-32lui986xEA3zx85-0M6jei3gnv6MLp90XZZF0Zi25UmU9fg52ZfzXpkGSLPw7/s320/phone+call+hack+3.PNG)
![[Image]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiQB8rWhEeA0dobMx0D-LUZOMNCoB5k7lStgc8U6pm95U6lmj8bHAdZywPF_HjQXhaAXfCzSc65SH-Wd_ymnbMmY2l1G8MVYR7HUVWGj-tZXjnj08bBfKa0fn2E7-86VhXDBygEyR61pDWK/s320/phone+call+hack+4.PNG)
![[Image]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEicuKcBnlDod5DzZO-5-RKWkv22gdNQFFbiBp5d0MgyFxVo2u-D6jDObt9n3sW6x5lTK8iPppQLezY-YfzK68dDPY78D3gMfV86OGjm8qVBwmDxGUM5kYD5SDeOkNXyiG-5ItxV_3gYC_FT/s320/phone+call+hack+4.PNG)
![[Image]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiY7b2eCAOO7lJNCGwZm7qjMalcX9pfz89Mme-bCJsKIMlKk0YzirOeCfoPN5k4B7QVj01QPX03bDRxar9BYuGO2IFpnoaBFzQN4BSKE3dzjBF3LOdZmM2H2pazkvR-5sERk41dLca5Ddfm/s320/phone+call+hack+5.PNG)
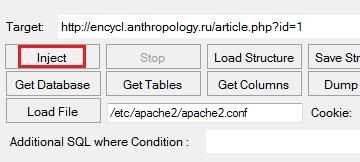
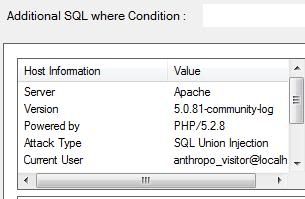
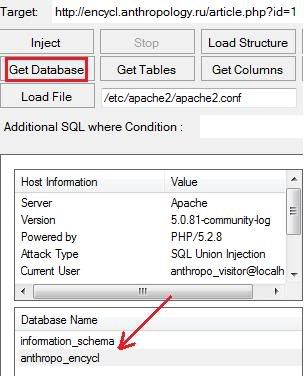
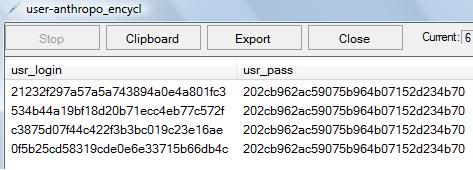
 An IP (Internet Protocol) address is as unique to a computer as a fingerprint is to us. An IP address enables one networked device to talk to the next. The downside of this inter-connectedness is that a logical location provided by the IP address is an open arms invitation to spammers and hackers. The art of war necessitates the importance of knowing who your ‘attacker’ is. Being able to trace an IP address to a PC is a direct way to remove the cloak of anonymity from a computer communicating with your own.
An IP (Internet Protocol) address is as unique to a computer as a fingerprint is to us. An IP address enables one networked device to talk to the next. The downside of this inter-connectedness is that a logical location provided by the IP address is an open arms invitation to spammers and hackers. The art of war necessitates the importance of knowing who your ‘attacker’ is. Being able to trace an IP address to a PC is a direct way to remove the cloak of anonymity from a computer communicating with your own.








 It happens to us all, sooner or later. We boot up our computer and *BAM* that’s it. Blue screen of death (BSOD). The hard drive has failed. But the baby shower pictures are on there! But my doctoral thesis is on there! But my fan fiction of Harry Potter Meets Captain Kirk is on there! But you’ve been making regular backups, right?
It happens to us all, sooner or later. We boot up our computer and *BAM* that’s it. Blue screen of death (BSOD). The hard drive has failed. But the baby shower pictures are on there! But my doctoral thesis is on there! But my fan fiction of Harry Potter Meets Captain Kirk is on there! But you’ve been making regular backups, right?


 Have you ever wondered how satellites can track mobile phones? It seems like they’re so far away, yet they can be accurate within about 15 meters. Just how is that done?
Have you ever wondered how satellites can track mobile phones? It seems like they’re so far away, yet they can be accurate within about 15 meters. Just how is that done?
 Interestingly, the entire Global Positioning System of satellites is run by the United States Air Force’s
Interestingly, the entire Global Positioning System of satellites is run by the United States Air Force’s  The new taskbar's default style does away with text labels and relies solely on program icons, therefore making better use of screen space. Its thumbnail previews--an improvement over Vista's--work well even when you have multiple windows open for one application. And the new Jump Lists feature gives you right-click access to context-sensitive menus of options (such as the ability to play shuffled music in Windows Media Player) even before you've launched an application. Even the nub on the right edge of the taskbar, which you can click to reveal the desktop, is a welcome, subtle enhancement. (One taskbar quibble: The border around running apps in the taskbar isn't a clear enough cue to distinguish between them and those that aren't currently active.)
The new taskbar's default style does away with text labels and relies solely on program icons, therefore making better use of screen space. Its thumbnail previews--an improvement over Vista's--work well even when you have multiple windows open for one application. And the new Jump Lists feature gives you right-click access to context-sensitive menus of options (such as the ability to play shuffled music in Windows Media Player) even before you've launched an application. Even the nub on the right edge of the taskbar, which you can click to reveal the desktop, is a welcome, subtle enhancement. (One taskbar quibble: The border around running apps in the taskbar isn't a clear enough cue to distinguish between them and those that aren't currently active.) The system tray--which is officially called the notification area, although I don't know anybody who calls it that--is no longer one of Windows' most aggravating "features." When you install new applications, any associated system-tray applets are cordoned off in a holding pen, where they can't clutter up the tray and can't use word balloons to pester you with information that you may or may not care about. You can also choose to have an applet appear in the system tray but in bound-and-gagged form, so it can't pop up messages. Microsoft has also dramatically reduced the volume of distracting messages from Windows itself, courtesy of Action Center, which queues up system alerts so that you can check them out at your convenience.
The system tray--which is officially called the notification area, although I don't know anybody who calls it that--is no longer one of Windows' most aggravating "features." When you install new applications, any associated system-tray applets are cordoned off in a holding pen, where they can't clutter up the tray and can't use word balloons to pester you with information that you may or may not care about. You can also choose to have an applet appear in the system tray but in bound-and-gagged form, so it can't pop up messages. Microsoft has also dramatically reduced the volume of distracting messages from Windows itself, courtesy of Action Center, which queues up system alerts so that you can check them out at your convenience. UAC is now tolerable: Windows Vista introduced User Account Control, which tries to warn you of attempts by viruses and other malware to tamper with your system. But it essentially has two settings: So Annoying You Click Without Thinking, and Off. In Windows 7, you get two intermediate settings that alert you only if a program changes settings, with or without the melodramatic screen-dimming effect. This new version is such a reasonable approach that it's even more mysterious how Microsoft could have botched the Vista version so badly.
UAC is now tolerable: Windows Vista introduced User Account Control, which tries to warn you of attempts by viruses and other malware to tamper with your system. But it essentially has two settings: So Annoying You Click Without Thinking, and Off. In Windows 7, you get two intermediate settings that alert you only if a program changes settings, with or without the melodramatic screen-dimming effect. This new version is such a reasonable approach that it's even more mysterious how Microsoft could have botched the Vista version so badly. HomeGroups are disappointing: HomeGroups sound like a nifty idea--a way to share folders full of media and documents between PCs across a network, so you can peruse photos stored on a desktop in the den from your laptop in the living room, for instance. But Microsoft's implementation is surprisingly half-baked: Rather than letting you specify a password during setup, for instance, it assigns one consisting of ten alphanumeric gibberish characters and tells you to write it down. And HomeGroups work only if all the PCs in question run Windows 7. A version that also worked on XP, Vista, and--dare I say it?--Macs would have been far cooler.
HomeGroups are disappointing: HomeGroups sound like a nifty idea--a way to share folders full of media and documents between PCs across a network, so you can peruse photos stored on a desktop in the den from your laptop in the living room, for instance. But Microsoft's implementation is surprisingly half-baked: Rather than letting you specify a password during setup, for instance, it assigns one consisting of ten alphanumeric gibberish characters and tells you to write it down. And HomeGroups work only if all the PCs in question run Windows 7. A version that also worked on XP, Vista, and--dare I say it?--Macs would have been far cooler.  Will hardware companies take to Device Stage? This new feature gives your printer, camera, and other peripherals information centers of their own, which hardware manufacturers can customize with features such as links to online manuals and troubleshooting tools. But unless companies invest the time to build useful Device Stages, this could be another Microsoft bright idea that doesn't go much of anywhere. Also, parts of Device Stage look short on substance (giant photorealistic renderings of your peripherals!) and others look potentially irritating (printer companies hawking ink cartridges right inside your OS!). All in all, I don't think it'll be a tragedy if Device Stage doesn't catch on.
Will hardware companies take to Device Stage? This new feature gives your printer, camera, and other peripherals information centers of their own, which hardware manufacturers can customize with features such as links to online manuals and troubleshooting tools. But unless companies invest the time to build useful Device Stages, this could be another Microsoft bright idea that doesn't go much of anywhere. Also, parts of Device Stage look short on substance (giant photorealistic renderings of your peripherals!) and others look potentially irritating (printer companies hawking ink cartridges right inside your OS!). All in all, I don't think it'll be a tragedy if Device Stage doesn't catch on.




